nextID
A trustworthy platform for managing citizens' digital identity information with a distinct geometric visual language.
Background
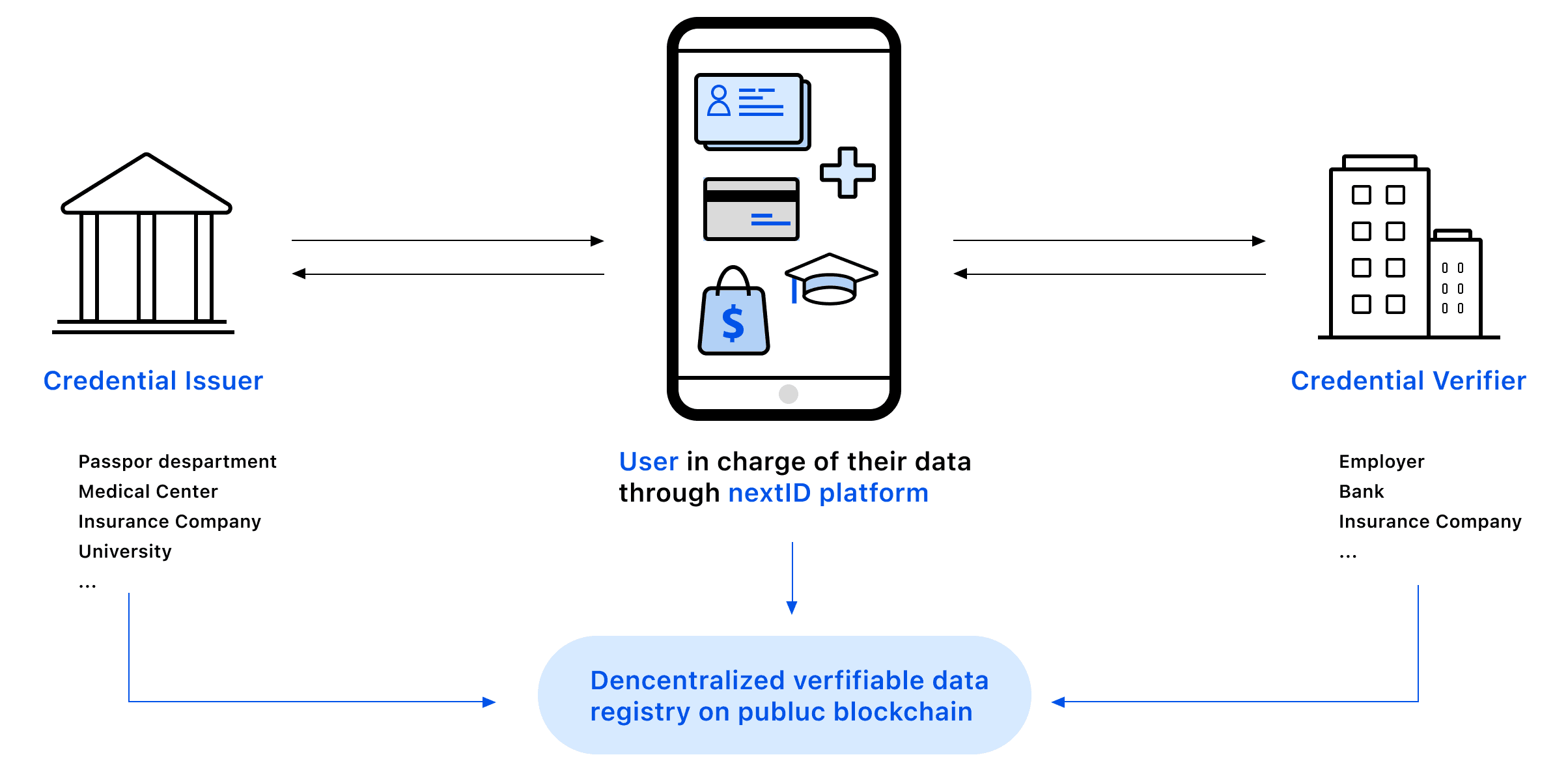
Digital identities are exposed in this information age. No on can be sure where his/her personal information is scattered. We believe that everyone should have full control over their digital identity, including how personal data is collected, used and shared.
By introducing the concept of decentralization into identity management, we can not only guarantee the security of collecting and storing personal information, but also enhance the efficiency of information exchange and transmission.
Identicial Problems
A Better Solution to
manage your personal Data
Design Challenage

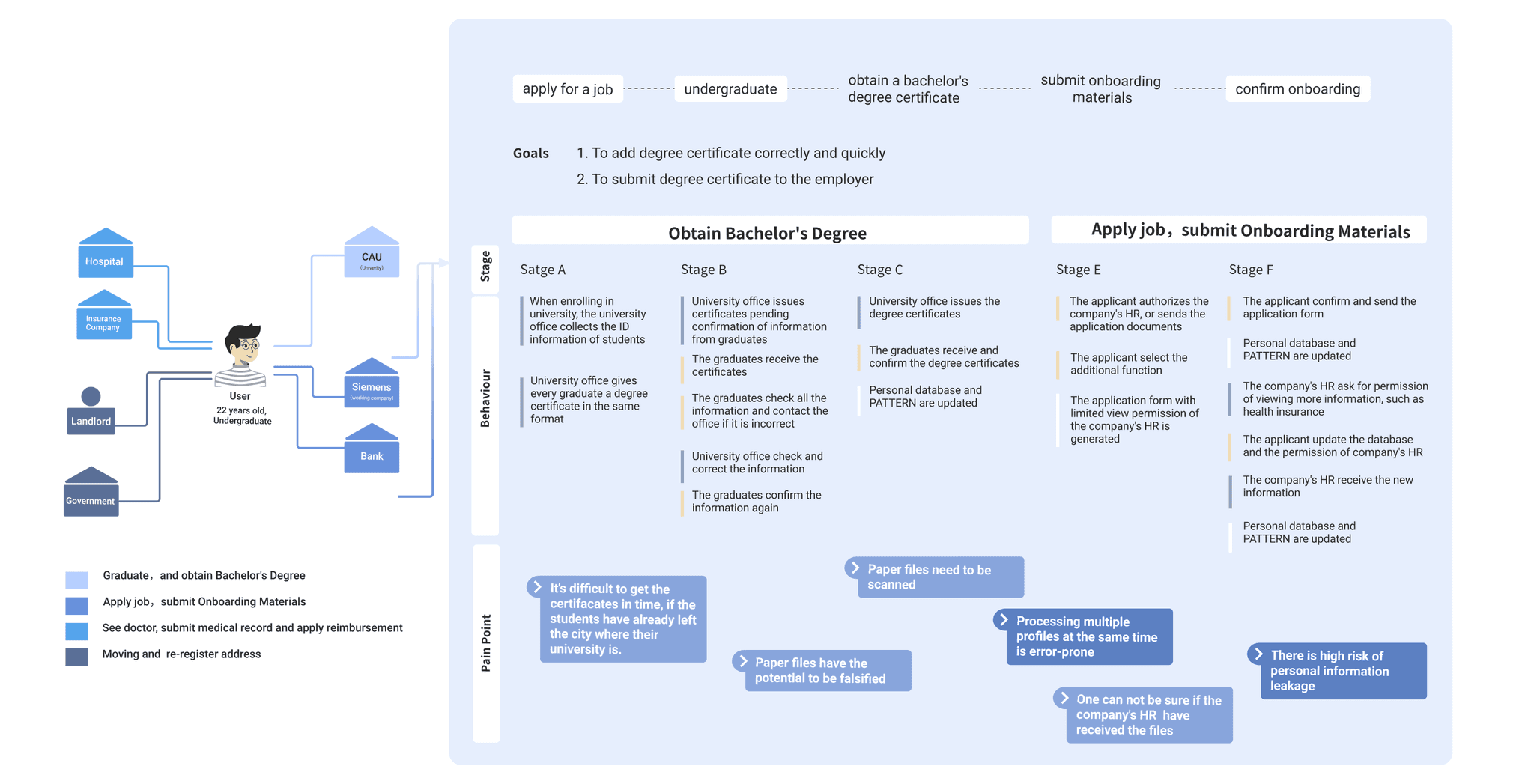
How to design a smooth process for adding and presenting credentials?

How to get users to trust the complex mechanisms behind it and the security of the platform?
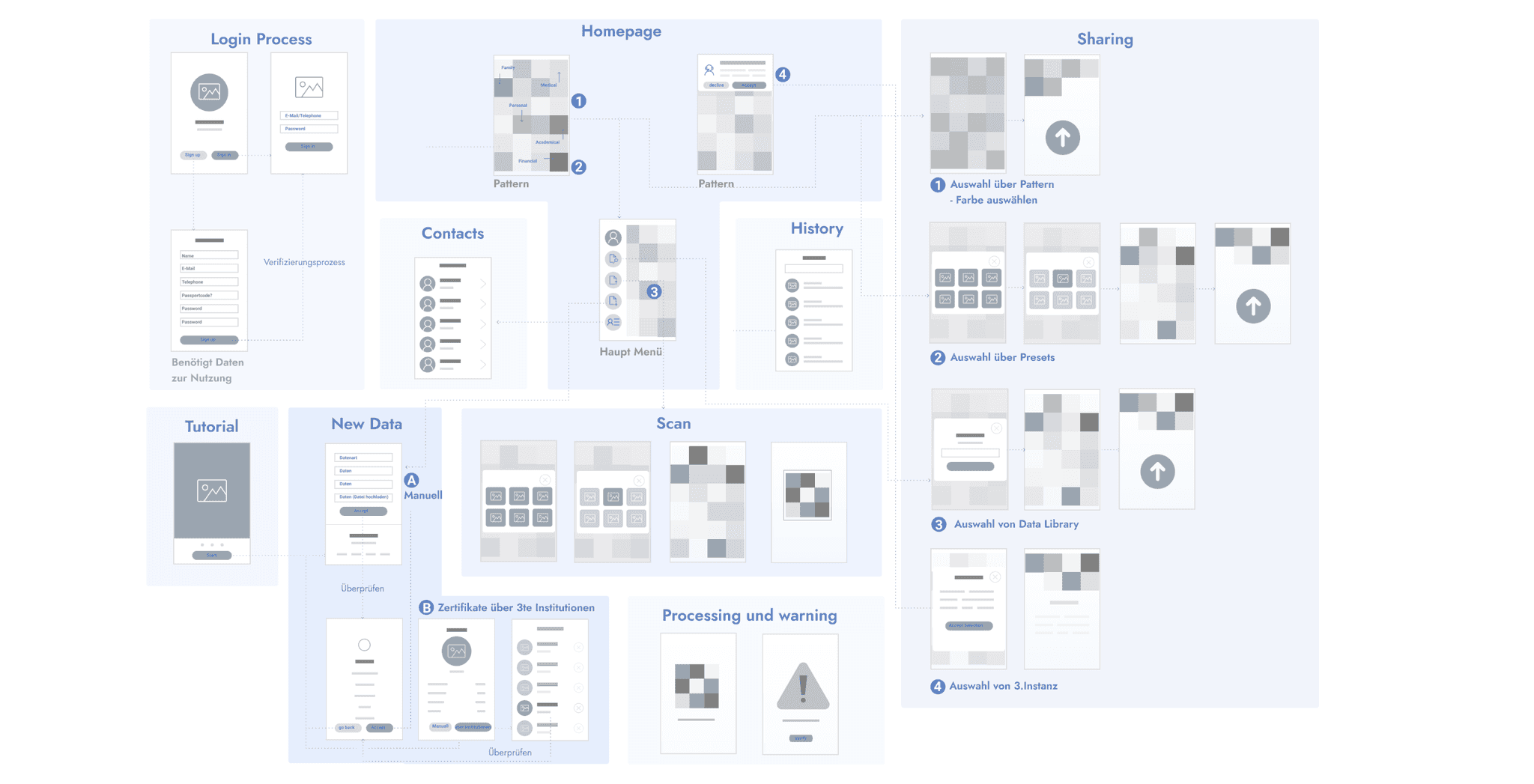
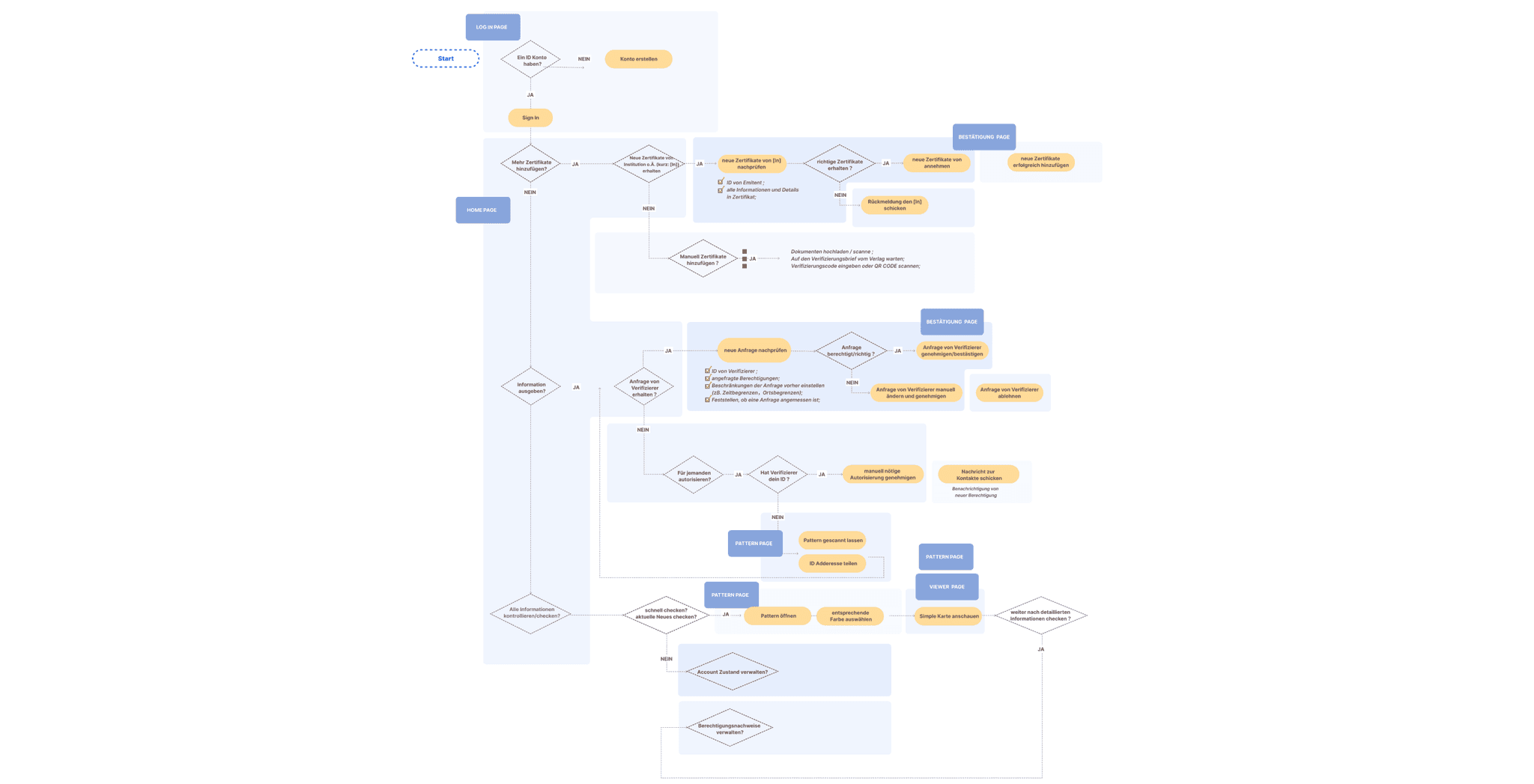
UX Development
The launching of NextID
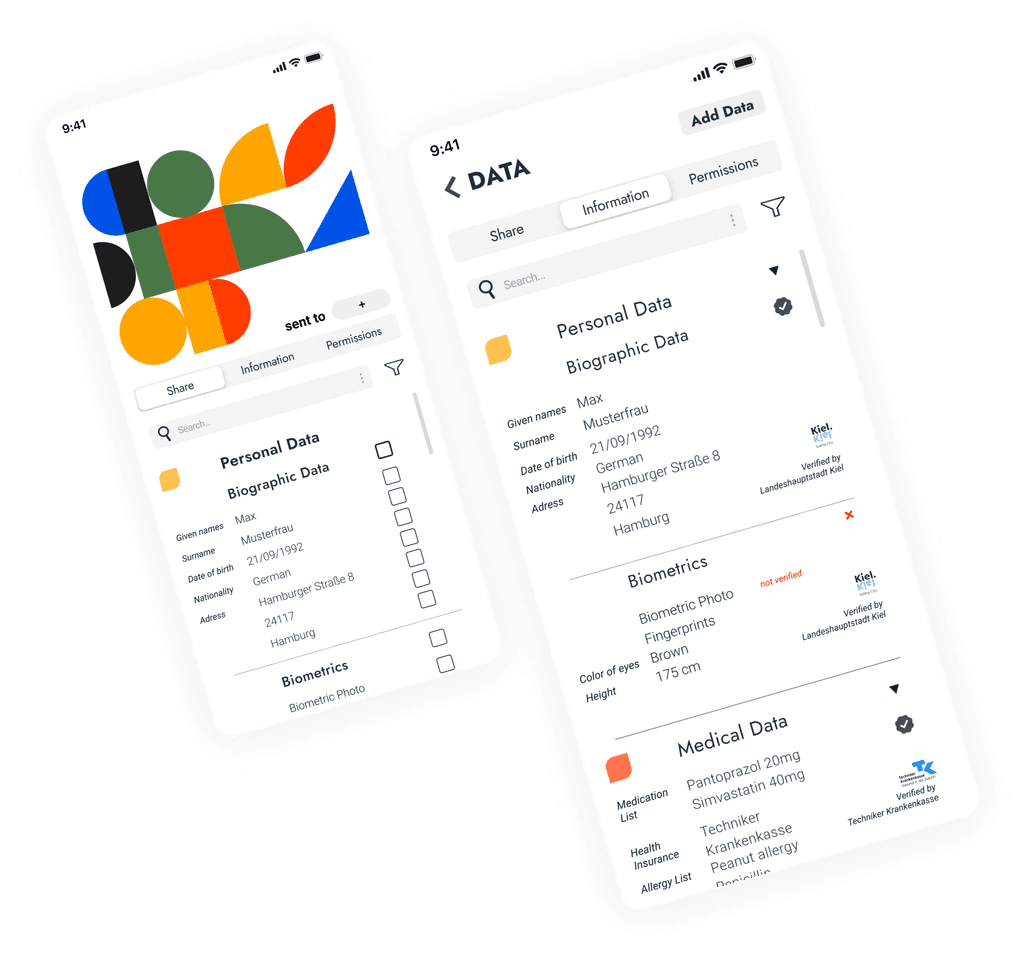
The NextID concept enables a sovereign management of everyone’s digital identity based on blockchain technology. It represents an alternative to today's monopolistic data economy. By digital identity we comprehend personal data, such as biometric data, educational certificates or medical data, etc.
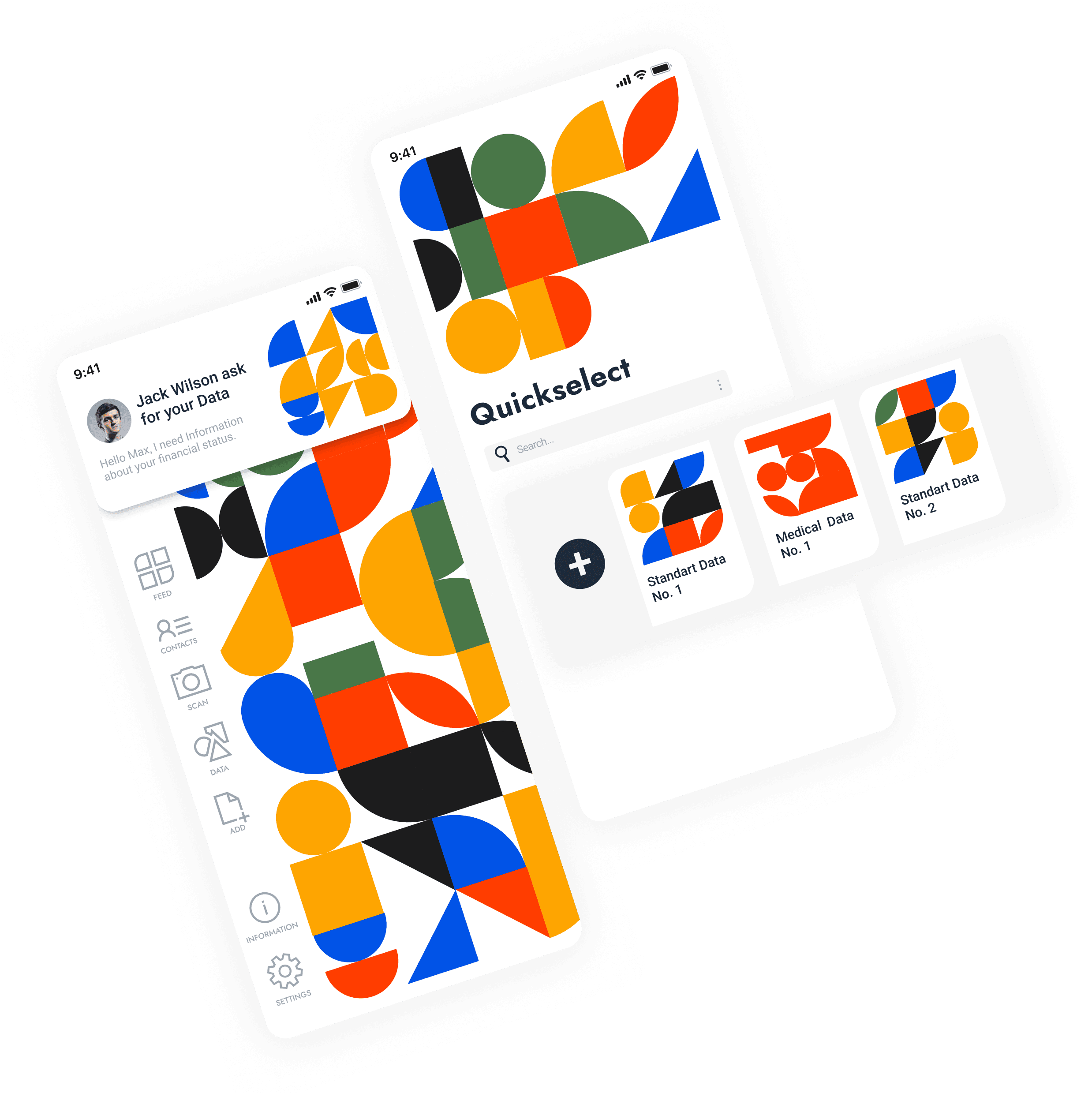
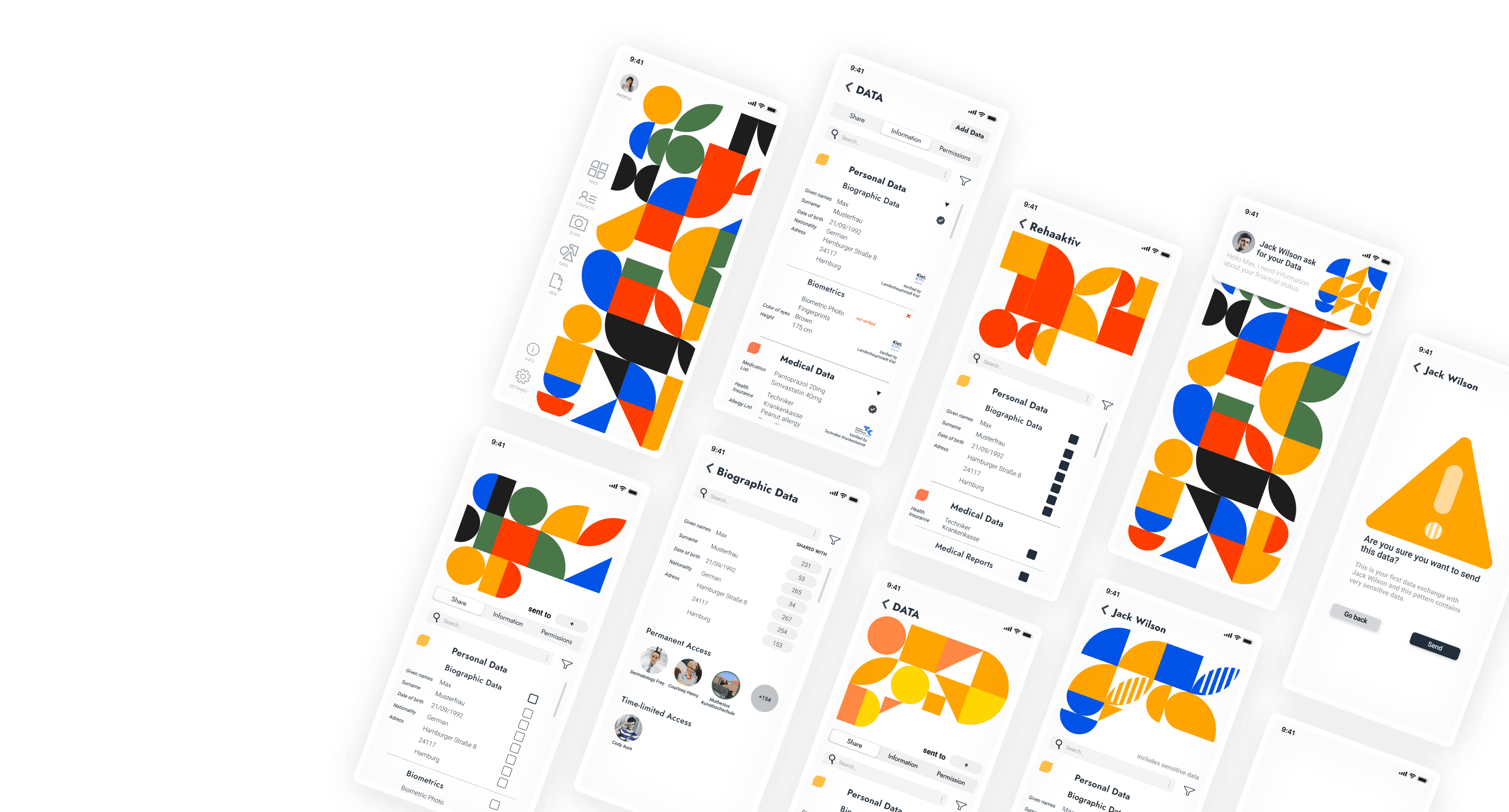
Eye-catching PATTERN represent Catogory of data
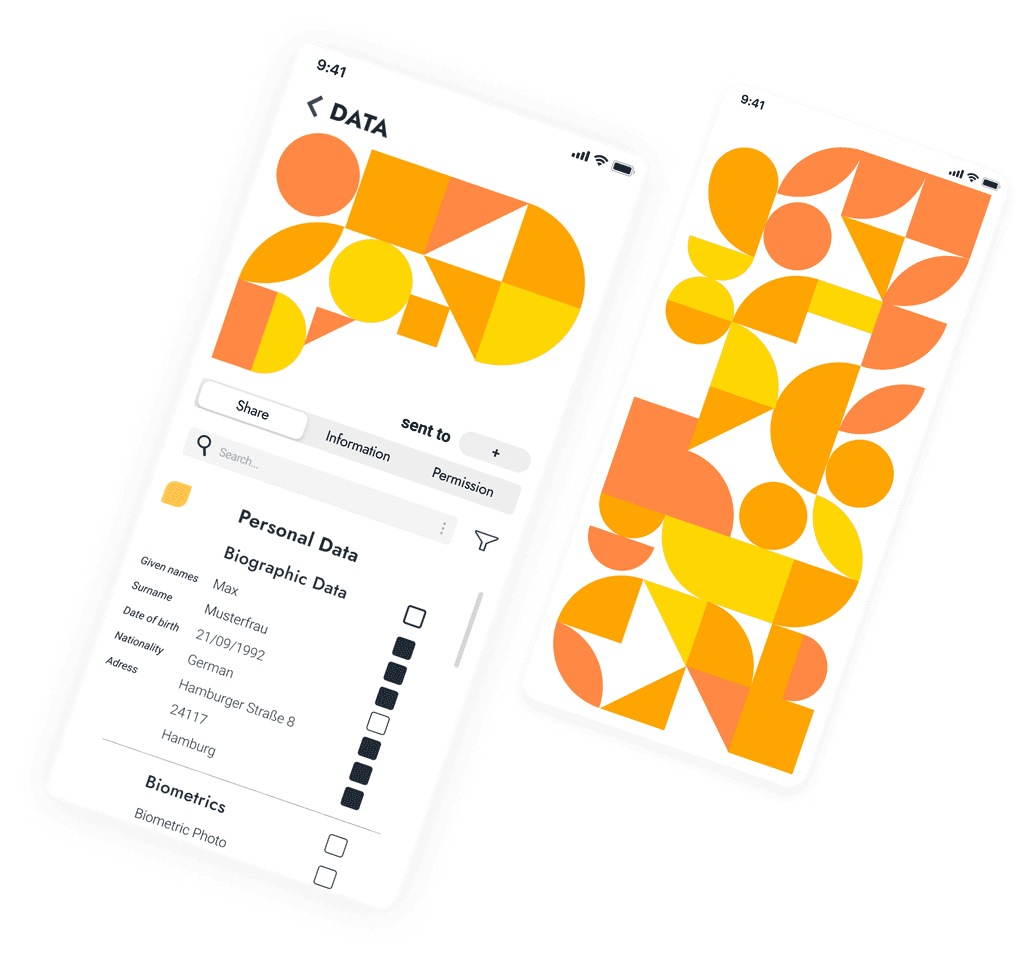
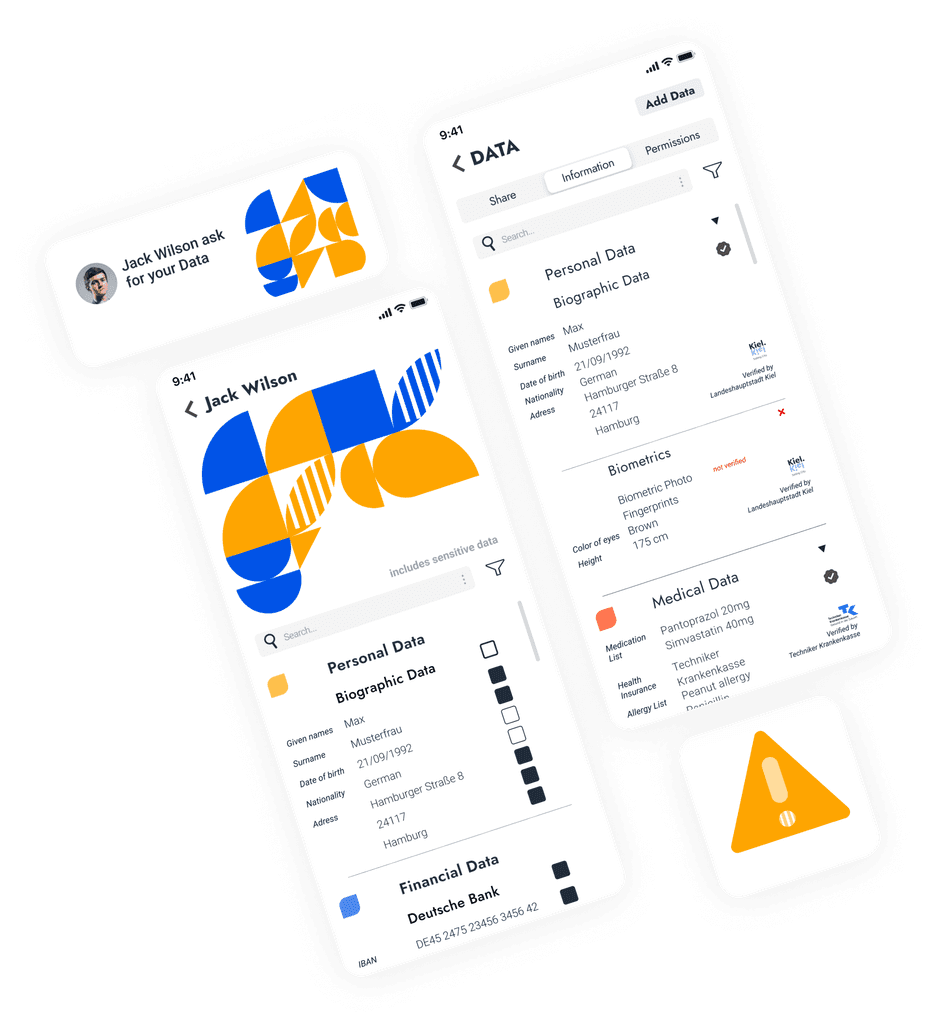
Home screen shows the individual pattern of each user. With the pattern it is possible to filter and select the data types by tapping on one or more colors. With a swiping motion, the pattern can be moved halfway up and the selected data is displayed in a list in the lower half of the screen.
Quick select, using color as filter
When user selects one color, it changes immediately into this color’s PATTERN through the aniamtion. It’s like a filter. And than user can go one select the exact documentation.
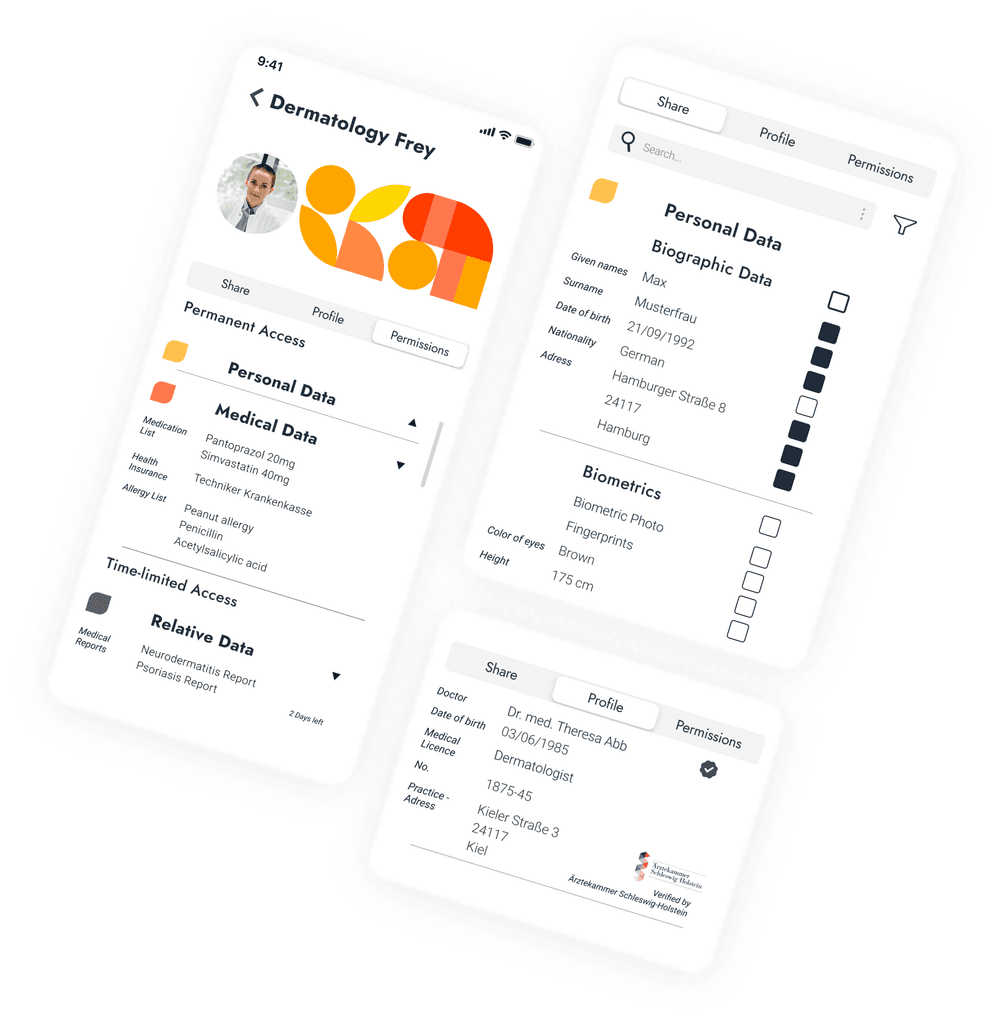
Authorize Data, Edit Permissions
Information is being securely authorized.
Security alert appears when information is shared with insecure third parties
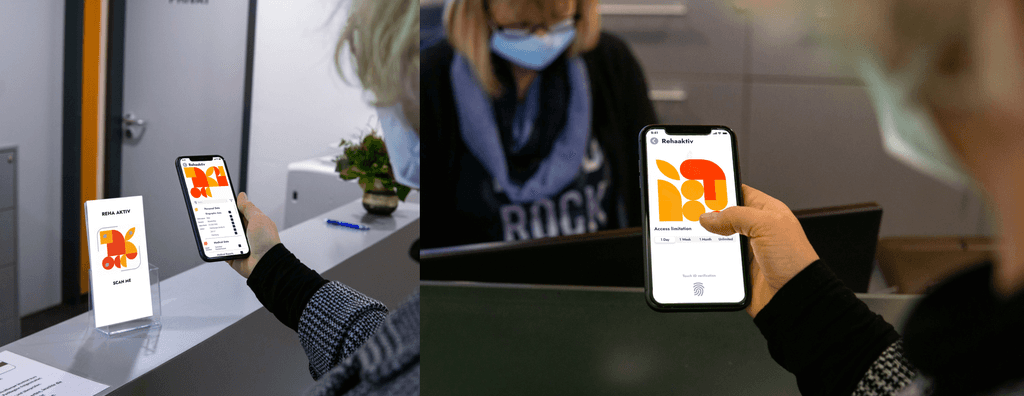
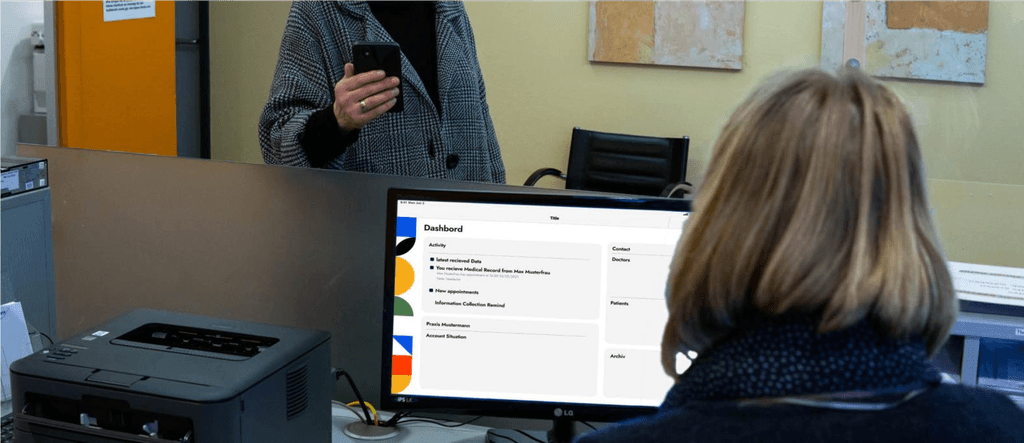
nextID Scenario
A simulation of the future where people use nextID to quickly register at hospitals, share cases with doctors and update their medical information.
About PATTERN
Transforming complexity into color blocks
To achieve identity autonomy, it is important not only to improve the information encryption system, but also to make users feel in control of their digital identity.
Therefore, by visualizing the encryption system and transforming the changing key string into a visual and dynamic geometric figure, the user can "see" the system working in an orderly manner, thus achieving a positive psychological implication.